BY COL MIKE ADAMSKI AND COL MATTHEW HARDMAN
Introduction
Decades of parochialism within the U.S. military fostered isolated digital networks that force the user to serve as integrator, squandering organizational energy and intellect. For the past 18 years, the U.S. and our partners have been fighting counterinsurgency and counterterrorism wars in Iraq and Afghanistan. In these theaters, arcane methods of digital collaboration with complicated workarounds became the norm, but our ability to set favorable conditions for operations mitigated the egregious distraction of outdated networks. In other words, we got away with it. We are unlikely to be so fortunate against adversaries like Russia or China that can match or exceed our capabilities. The ability to rapidly synthesize data to inform decision-making across all echelons and domains is necessa
The services lack the ability to effectively communicate – whether internally, amongst one another, with the intelligence community, or with multinational partners. The DoD needs to establish joint data standards with the goal of creating commonly-accessible data. Without commonly-accessible data, the U.S. military will not realize the potential of 21st-century technologies. We remain too reactive and slow to mitigate risk and seize opportunities,[1] and our function- and service-centric infrastructure prevents digital collaboration.
The Myths
It’s important to acknowledge a few myths associated with the U.S. military’s digital networks. The first is that information technology can eliminate the fog of war. War is still a human endeavor, and human beings still suffer from cognitive biases and faults. Second, that the joint force already possesses a collaborative digital environment to support command and control; this is not the case. Commanders and staffs in all services and echelons cannot digitally collaborate with other services and are often unable to do so within their own organizations. Solutions remain service centric. Hollywood portrays the military with an awareness, a speed, and an interconnectedness that does not exist, but could. The third and final myth is that the DoD has failed to leverage modern technology; this is untrue. The DoD has been successful with digital solutions to discrete problems, but it has never committed to solving the problem of true joint interoperability.
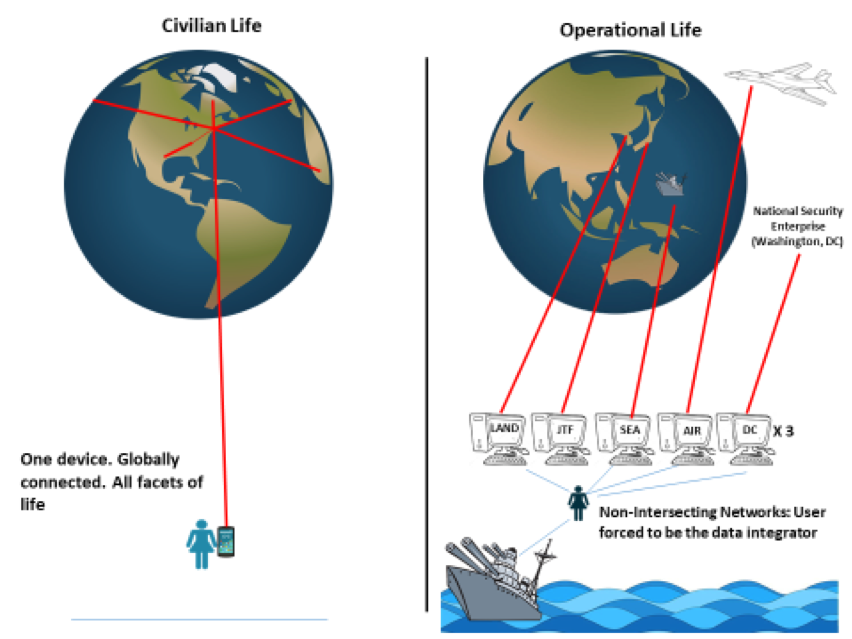
Civilian vs. Warfighter Capability – A Stark Contrast
The contrast between capabilities available to a warfighter in their civilian and operational lives is stark. Imagine CAPT Sue Smith, U.S. Navy a warship driver, going on vacation. She can book various forms of transportation, navigate, shop, stream entertainment, play on-line games, get weather updates, connect with friends, find information about her destination, and execute a whole host of other functions. The hardware platform is largely irrelevant, and the information is intuitively available, usable, and shareable because the underlying software makes it possible due to commonly-accessible data. CAPT Smith’s experience at sea on her warship is much different. To maintain operational understanding, she relies upon scores of discrete systems that do not talk with one another. Often, she and her staff have to “swivel chair” information between stove-piped systems, or simply try to piece it together in the operations center. In Sue’s operational existence in the Navy, she is forced to be the integrator of data, a requirement that does not exist in her civilian life where many of these mundane tasks are easily automated. Machines can relieve users of some functions to allow them to concentrate on other cognitive functions; we do this in our daily lives through a Google search for restaurants or our contacts lists. The assistance that machines provide to our daily thinking is so ubiquitous that we take it for granted; often, that assistance is missing from our operational lives.
Service Parochialism
Notable military historian Martin Van Creveld observed that “the cardinal result of technological innovation over time has been a vast increase in the amount of information needed to run any military unit, make any decision, carry out any mission, or conduct any operation, campaign, or war.”[3] This information largely flows through different systems that rarely talk to one another. Mitigating this problem requires middleware, ad hoc solutions, and user manual manipulation to achieve integration – ensuring slow, inefficient, and incomplete use of information.
Stovepipes exist because each service and agency are responsible for developing and acquiring their own systems. Parochial preferences and traditions outweigh aggregate requirements, leaving the user to achieve integration and interoperability through unnecessary ingenuity and hard work. This dynamic pre-dates the digital era and persists, despite hard lessons from the Iran Hostage Rescue, Grenada, Desert Storm, and even 9/11. While the Goldwater-Nichols Act of 1986 increased service coordination, it has minimally impacted the development and acquisition processes. In Afghanistan and Iraq, as one general officer put it: “our enemies never forced us to change.” Where change occurred, it was largely through reorganization and ad hoc work-arounds.
The foundation of a joint digital environment is commonly-accessible data. Commonly-accessible data enables integration from inception, rather than our continued reliance on additional layers of software that serve as bridges for systems or databases on a network. This layering, also known as “middleware,” is a time-honored technique for integrating disparate warfighting function and service systems – despite slowing processing and creating seams, vulnerabilities, and roadblocks. System shortcomings force the user to become the integrator. With both of these methods, “what passes for good systems
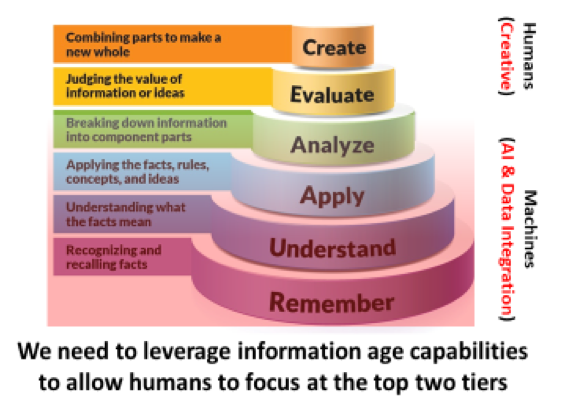
Current systems focus on the needs of domain and service function, not the user. DoD must unshackle the user by designing a system that is inherently integrated and interoperable. A modern network must transform information and data into actionable knowledge.[5] Effective integration allows users to focus on higher-impact activities, such as data-evaluation and decision-making.[6] Bloom’s Taxonomy usefully models this relationship by identifying automatable activities, which should serve as a goal for any integration initiative.[7]
The obstacles to commonly-accessible data are largely cultural rather than technical. From inception of digital adoption in DoD, there has been an acknowledgment that commonly-accessible data requires joint data standards – the key to system and platform integration. General David Perkins and General James Holmes have argued that we must shift from interdependence to integration in order to foster the joint-culture necessary for multi-domain operations.[9] With a service-centric approach to acquisitions, requirements and standards are often developed with little regard for interoperability.
Barriers – Risks – Challenges
Chris Colbert (Managing Director of the Harvard Innovation Labs), notes that 84% of digital transformational efforts and 95% of corporate innovations fail for three reasons: 1) Those trying to solve the problem don’t really understand the problem they’re trying to solve, 2) The solution which is attained doesn’t actually solve the problem, and 3) Those trying to solve the problem don’t really understand the needs of the customer.[10] Additionally, innovation entails risks and challenges; it incurs economic, organizational, and opportunity costs. The benefits of the innovation must be significantly greater than the status quo and must obviously warrant the risks.[11] There are a number of compelling risks and challenges associated with establishing a digital network of this magnitude.
Security
Internationally-renowned security technologist Bruce Schneier notes that “the [digital] attacker has the advantage for several reasons,” most notably that “complexity is the worst enemy of security” and “an attacker can choose a particular attack and concentrate efforts, whereas the defender has to defend against every possibility.”[12] Given the extent of DoD’s operations, it will inevitably be less agile than attackers, who can pick and choose the weakest links without warning.
The Burden of Legacy Systems
Legacy systems pose challenges to reform. Writing about military data management, Dr. Marion Ceruti noted that “the single most challenging obstacle in DoD data management is the seamless integration of legacy information systems at all levels of heterogeneity. … [I]ntegrating multiple legacy databases or developing interoperable information exchanges between legacy databases is slow, difficult, and expensive.”[13] Reformers must evaluate each legacy system on the basis of efficacy and cost of integration; many systems will have to be replaced or upgraded to achieve compatibility.
Historical Lessons of Innovation
Military historian and theorist Paul Kennedy concluded that great victories require “a support system, a culture of encouragement, efficient feedback loops, a capacity to learn from setbacks, and ability to get things done.”[14] The advancing capabilities of Russia and China have clarified the threat, and emerging multi-domain doctrine dictates the operational approach of deterring, contesting, and defeating those adversaries – but the adaptation of defense organizations and processes remains a challenge.
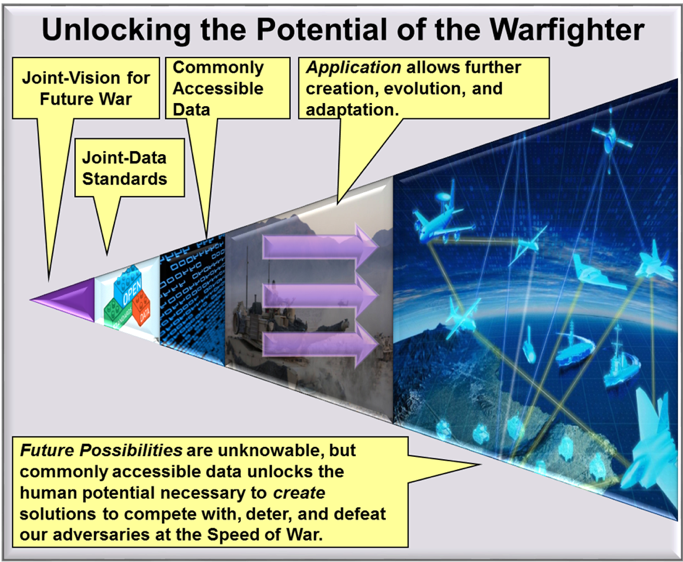
Despite the human brilliance and resources available to the DoD, history suggests that no single team is going to facilitate the global multi-domain convergence. The requirements, challenges, and scope are too daunting. The history of innovation suggests this is both normal and acceptable. Malcolm Gladwell argued that, contrary to the popular perception, Steve Jobs was not an inventor but a “tweaker.” Others invented the portable digital music player, the smart phone, and tablet, but Jobs adapted, evolved, and refined those products into something fundamentally better.[16] In the Second World War, the Allies gained air-superiority over Western Europe because they had resources, had gotten many of the big ideas right, and had been able to adapt and “tinker.” They modified the P-51 Mustang with the Rolls-Royce Merlin engine and added disposable drop tanks, further tipping the balance in their favor.[17] Committing to interoperability through joint data standards is the “big idea” that can create the space and potential for further adaptation. Digitally-savvy operators in an environment of commonly-accessible data will be able to adapt, evolve, refine, and create modest solutions that are fundamentally better than the status quo.
Recommendations
Kathleen J. McInnis writes that there is consensus regarding the “joint and interagency” problem, but there is no consensus on a solution.[18] Working backwards from strategic and operational problems might better highlight the institutional and organizational challenges to overcome.
1. Communicate and Implement the Vision for Joint Data Standards: The DoD CIO has provided a clear vision for digital integration and laid the foundation for joint compliance via a modular open systems approach memorandum signed by all service secretaries in January 2019. We recommend that the vision continue to emphasize the need for adherence to joint data standards that facilitate commonly-accessible data to place the user at the center of the operational network, thus freeing the user from the burdensome task of integration. It must avoid fixating on niche service or function specific solutions. With new authorities, the DoD CIO is uniquely empowered to drive change. This needs to be a deliberate and relentless pursuit of shared understanding and disciplined execution. Commanders and operators are the critical change agents that must ensure execution. There must be recurring formal action to revisit the original vision to ensure it remains on a successful trajectory.[19]
2. Conduct Joint Command and Control Wargames: The U.S. conducted the Louisiana Maneuvers in 1941 to improve the readiness of tactical formations and operational headquarters. They also served “as field laboratories for the armored, anti-tank, and air forces that had come of age since 1918.”[20] A series of well-resourced “Modern Louisiana Maneuvers” against thinking free-play adversaries would help better define the MDO requirements necessary to successfully deter, contest, and defeat those adversaries. These simulations should experiment with “instruments and organizations”[21] that are feasible but do not currently exist, such as a digital command and control network. The original Louisiana Maneuvers did this and not only allowed the development and refinement of requirements, but also allowed commanders to imagine the possibilities of future battlefields. Current commanders may not fully understand what they are currently missing. As a precursor to joint command and control wargames, we can leverage existing service and joint exercises to capture enduring struggles with integration into a compelling video documentary to proliferate a common understanding of the problem we’re trying to solve: the lack of effective digital collaboration at the speed of war.
3. Conduct Security and Legacy System Assessment: Assess impacts of maintaining legacy systems in terms of capability, near and long-term costs as well a current security. The services must provide this feedback in order to make informed decisions about replacement, timelines, and interim-bridging solutions. The 2018 defense authorization bill mentions a “bar on DoD organizations from buying or developing technologies that won’t adhere to joint standards, and tells the CIO to draw up “mitigation plans” for systems that already do not.”[22] Shared acquisitions foster a culture in which individual operators and implementers can explore system capabilities, “tinker,” and innovate.
Conclusion
There is real momentum for change. The expansion to DoD CIO’s authorities, the Department’s strategy for digital transformation, and service leaders’ words and actions signal a change in the information-sharing mindset. One of the greatest challenges is maintaining focus and commitment over a decade or more of leadership changes. Russia and China’s increased capabilities provide greater clarity regarding the operational problem, and a nascent doctrinal approach in multi-domain operations provides the focus necessary to successfully innovate. Commonly-accessible data is feasible; information-technology partners across industry, the DoD, and academia have many of the technical solutions. Most importantly, the users at the center of the network possess the curiosity, intellect, and passion to not only make the next evolution of digital innovation succeed, but to make it extraordinary.
COL Mike Adamski (U.S. Army) recently completed the National Security Fellowship at the Harvard Kennedy School of Government. His previous operational assignment was as the senior intelligence officer for the 82nd Airborne Division. He is currently working on the Operation Resolute Support staff in Kabul, Afghanistan.
Colonel Matthew Hardman served as a National Security Fellow at the Harvard Kennedy School, AY18-19. He is an infantry officer that most recently served as an Observer Controller at the National Training Center in California and as a Battalion Commander in Alaska.
Edited by Hugh Verrier
Photo by Margaret Weir
[1] Transforming the Department of Defense for Agile Domain Command and Control, (Draft) Douglas O. Creviston. Pg. 1.
[2] Figure made by authors, using image drawn from publicdomainvectors.org. Embedded image citation: 316 Globe Free Clipart, “Public Domain Vectors (Embedded Globe Images Drawn from Free Clipart),” n.d., https://publicdomainvectors.org/en/tag/globe.
[3] Martin Van Creveld, Technology and War: From 2000 B.C. to the Present (New York : London: Free Press; Collier Macmillan, 1989), 237.
[4] M.G. Ceruti, “Data Management Challenges and Development for Military Information Systems,” IEEE Transactions on Knowledge and Data Engineering 15, no. 5 (September 2003): 1061, https://doi.org/10.1109/TKDE.2003.1232263.
[5] Arthur K. Cebrowski and John J. Garstka, “Network Centric Warfare: It’s Origin and Future,” Proceedings, January 1998, 2.
[6] Arthur K. Cebrowski and John J. Garstka, “Network Centric Warfare: It’s Origin and Future,” Proceedings, January 1998, 2.
[7] Mary Forehand, “Bloom’s Taxonomy,” Emerging Perspectives on Learning, Teaching, and Technology, accessed March 2, 2019, https://www.d41.org/cms/lib/IL01904672/Centricity/Domain/422/BloomsTaxonomy.pdf.
[8] Jessica Shabatura, Bloom’s Taxonomy Image, n.d., n.d., https://tips.uark.edu/using-blooms-taxonomy(Base image drawn from report, text added by authors).
[9] David G Perkins and James M Holmes, “Multidomain Battle: Converging Concepts Toward a Joint Solution,” Joint Forces Quarterly 88, 1st Quarter 2018 (2018): 4.
[10] Chris Colbert, “Technology Is Dead – Presentation, Singapore Fintech Festival” (November 13, 2018), http://www.chriscolbert.com/.
[11] Ibid.
[12] Bruce Schneier, Data and Goliath: The Hidden Battles to Collect Your Data and Control Your World, First edition. (New York, N.Y.: WWNorton & Company, 2015), 164.
[13] Ceruti, 1061.
[14] Kennedy, 372.
[15] Figure made by authors, using image drawn from Lockheed Martin. Embedded image citation: Lockheed Martin, “Lockheed Martin Introduces Mission Planning System That Connects Systems and Assets Across Domains (Image embedded within slide drawn from Article),” September 17, 2018, https://news.lockheedmartin.com/2018-09-17-Lockheed-Martin-Introduces-Mission-Planning-System-That-Connects-Systems-and-Assets-Across-Domains?_ga=2.199667308.3766207.1560300725-322018779.1560300725.
[16] Malcolm Gladwell, “The Tweaker: The Real Genius of Steve Jobs.,” The New Yorker, November 14, 2011, https://www.newyorker.com/magazine/2011/11/14/the-tweaker; Kennedy, Engineers of Victory, 370–71.
[17] Kennedy, Engineers of Victory, 125–27.
[18] Kathleen J McInnis, “Goldwater-Nichols at 30: Defense Reform and Issues for Congress,” N.D., 1.
[19] GEN (Ret) David Petraeus, “Roundtable Discussion with National Security Fellows, Harvard University” (September 19, 2018).
[20] Christopher Gable, The U.S. Army GHQ Maneuvers of 1941, CMH_Publication_70-40-1 (Washington, D.C.: Center for Military History, 1991), 5.
[21] Ibid.
[22] Jared Serbu, “DoD CIO Gets Beefed-up Authorities, Responsibilities Starting Jan. 1.”